VPNs and Privacy
Do VPNs provide a single point of failure? If so, isn't that a security concern we should be worried about?
Recently I was asked a question regarding the privacy that VPN’s provide and whether they are a good security measure. The reason for this was the single source of failure (or breach point) that using a VPN introduces. If an attacker was able to gain access to the VPN server, then they would have full access to all of your internet traffic (since it’s decrypted at the VPN server).
This is a very valid point.
If I had my VPN turned on ALL the time, then all of my traffic would be sent to a single point which, should that server be compromised or the owner of the server have bad intentions, it would mean that my data is compromised.
In a recent blog post about how VPNs work, I introduced some of the benefits of using a VPN. One of these points was the ability to access region-specific content. Although gaining their popularity through this beneficial aspect, VPNs are not the only way to access region-specific content.
Without diving too deep into a what a proxy is (I’ll explain it in a later post), it can be (for this case) be described as a VPN without the secure tunnel (unencrypted).
This then raises the question:
What role do VPNs play in privacy and security if we can access region-specific content other ways AND using a VPN introduces a single-source of failure?
It’s all about trust.
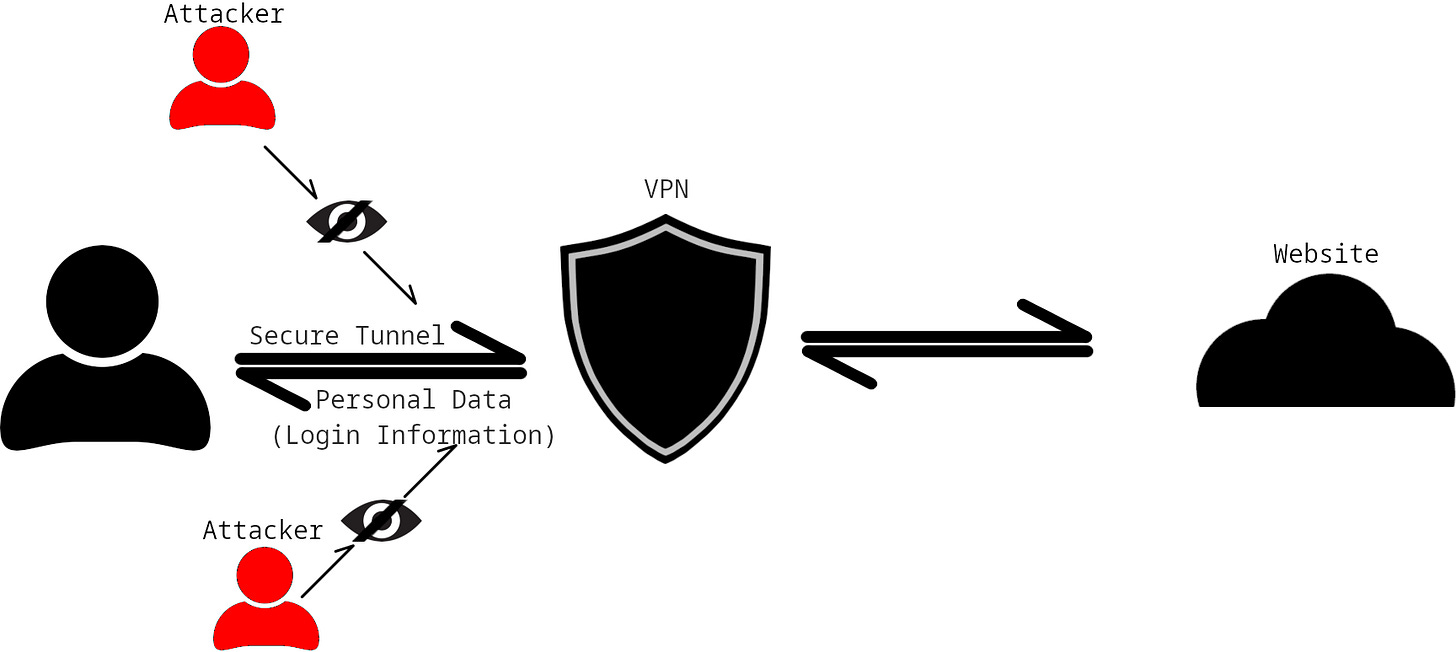
VPNs and their secure tunnels allow those on the same network as you (and everyone up the VPN server [including your ISP]) from viewing the data that you send (for example, your login details) and where you send that data (for example, which website). When using public WiFi, the biggest threat is an attacker or someone with a computer that’s been compromised (with a virus) on the same internet as you.
Diagram showing an attacker attempting to read data sent from a user with a VPN activated.
To understand this better, I’d recommend reading my previous post first which dives into what VPNs are and how they work.
One simple way to counter these threats would be to encrypt your data and hide where you’re sending it to; which is achieved with a VPN.
It seems to come down to protecting yourself from whatever is a bigger threat to your security and privacy.
Choosing the right VPN service is important. I’ll be releasing a blog soon about recommendations and what to look for when choosing a VPN service, but for now, my recommendation would be to look into ProtonVPN.
Recommendations
Public Wifi
If you’re using public wifi, then you should 100% use a VPN. There are many guides and proof of concept videos on the internet to show how easy it is for someone to access your unencrypted data on public wifi.
Home Network
If you’re using your hsome network, it’s actually recommended that you don’t use a VPN (unless it’s for region-specific content or you don’t trust the website you’re visiting). This is because of the concerns mentioned above about the single point of failure.
Mobile Data
If you’re using your mobile data / personal hotspot you probably don’t need to (although it might be good) practise to. While I’ve heard of security and privacy issues on mobile data (3G, 4G & 5G), I haven’t been able to find any proof of concepts or articles about this (in similar usage to public wifi hacking).