What is Multi-Factor Authentication?
Data breaches and increased security policies have prompted companies to implement multi-factor authentication across their users. But what is it? Are some forms better than others?
Multi-Factor Authentication (MFA) isn’t a new term. Essentially, it means providing more than one way of authenticating yourself. How this might look in terms of cyber security, is entering a password and entering a 6-digit pin.
What are some examples of Multi-Factor Authentication?
Multi-Factor Authentication can come in many forms. Typically there’s a preference to call two forms of authentication (such as the example above) two-factor authentication (2FA). For the sake of simplicity, this blog will be referring to them as equivalent.
Since MFA is simply multiple forms of authentication, a better question would be to ask what are examples of authentication used as an extra step in the MFA process. Anyways, here’s a compiling some of the common ways MFA is implemented:
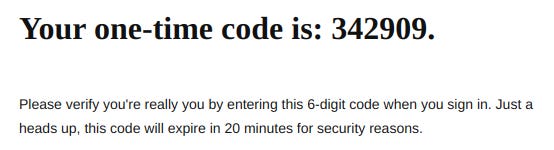
OTP (One Time Password)
These can be found in emails and text messages and are valid for only one login, expiring on use.
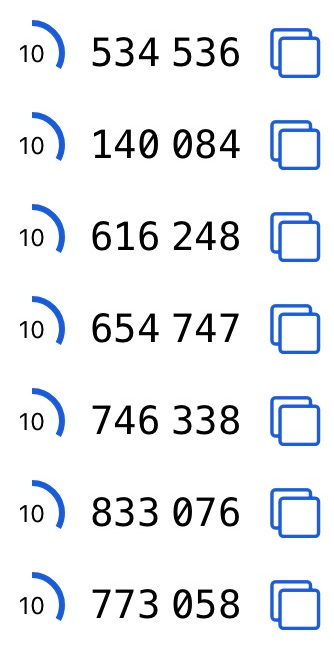
TOTP (Time-based One Time Password)
TOTPs are the pin codes that you’ll find in your authenticator apps (Google Authenticator, Authy, Microsoft Authenticator, etc.) that change every 30 seconds. These don’t expire on use but can be used multiple times within the 30-second time period
.
Verification from a trusted device
These are typical for platforms that have an application or similar and have a known trusted device. These platforms require the known device (such as your phone) to verify that it’s you logging in from a new computer.
Biometric Verification
While this is less common as secondary authentication, it is a means of authentication that can be and has been used alongside pins, passwords, and other forms of authentication.
Email Verification
Differing from OTP, it’s becoming increasingly common for the platform you’re using to send through a link to be opened to verify the login attempt. With phishing becoming more and more prevalent, it’s important to be wary of the links sent to us by email or other means.
Secret Question Verification
While it’s much less common nowadays, a typical way of authenticating someone’s identity was for them to answer questions they had previously answered; questions such as “What is your mother’s maiden name?” or “What is the name of your favourite pet?” etc.
Are all Multi-Factor Authentication methods equal?
No, not all authentication methods are equal. Certain methods, such as secret question verification and even OTP sent via text messages are weaker than other means such as TOTP or verification from a trusted device.
Hopefully, when required to set up MFA for your login, you are given the option of multiple means - whether that be by receiving a text message or by setting up a code-generator app. While both methods inevitably make your account harder to log into, it’s important that there’s a level of understanding of which method is better.
SMS text verification is notoriously simple to crack. KrebsOnSecurty released an article here describing a method used by some attackers to intercept SMS OTP codes. Forbes also released an article here describing the lack of security with these methods. With this in mind, one major takeaway is to avoid SMS verification and instead use TOTP (code-generator apps).
TLDR
Multi-Factor Authentication is simply a means of using multiple forms of authentication to verify a login of an account. These can come in the form of OTP, TOTP, emails, etc. It’s important to understand the differences in these implementations, but of note SMS verification (OTP) should be avoided, and instead, TOTP (code-generator apps) should be used.